Industry Insights
Phishing Campaign Likely Targeting IT Departments and Bypassing Email Filters
August 5, 2025 | 4 min read
Joshua Green and Thomas Elkins

The BlueVoyant Security Operations Center (SOC) recently responded to a client’s user accessing a potentially malicious link that further research identified as part of a recent, robust campaign aimed at stealing Twilio SendGrid credentials. The attack was investigated by BlueVoyant’s Threat Fusion Cell (TFC) to understand how it can bypass email filters, and how it likely targeted IT departments.
How the Twilio Phishing Campaign Works
Twilio SendGrid is widely used by organizations to manage both internal and external communications, delivering transactional emails such as password resets, system alerts, and billing notices, as well as marketing messages. Because it integrates with critical business systems and holds valuable data including contact lists, email templates and API keys, compromising a SendGrid account could allow attackers to send phishing or spam emails from trusted infrastructure, harvest sensitive information and bypass traditional email security controls. This makes Twilio SendGrid an attractive and high value target for threat actors seeking to conduct large-scale phishing or business email compromise (BEC) campaigns. BEC campaigns are sophisticated attacks that impersonate trusted individuals or entities to steal money or data.
During BlueVoyant SOC’s investigation, analysts identified a suspicious email with the subject line ‘Your Webhook is Failing’. The threat actor deliberately used ‘SendGrid’ as the email sender’s display name to disguise the true sender address.
The email content centered around a fabricated issue, claiming a SendGrid webhook was failing on the client’s end and SendGrid was unable to receive data. It then provided detailed instructions for diagnosing the supposed problem. At the conclusion of the message, the attacker included a phishing link disguised as a shortcut to the client’s ‘Webhook Settings’ page.
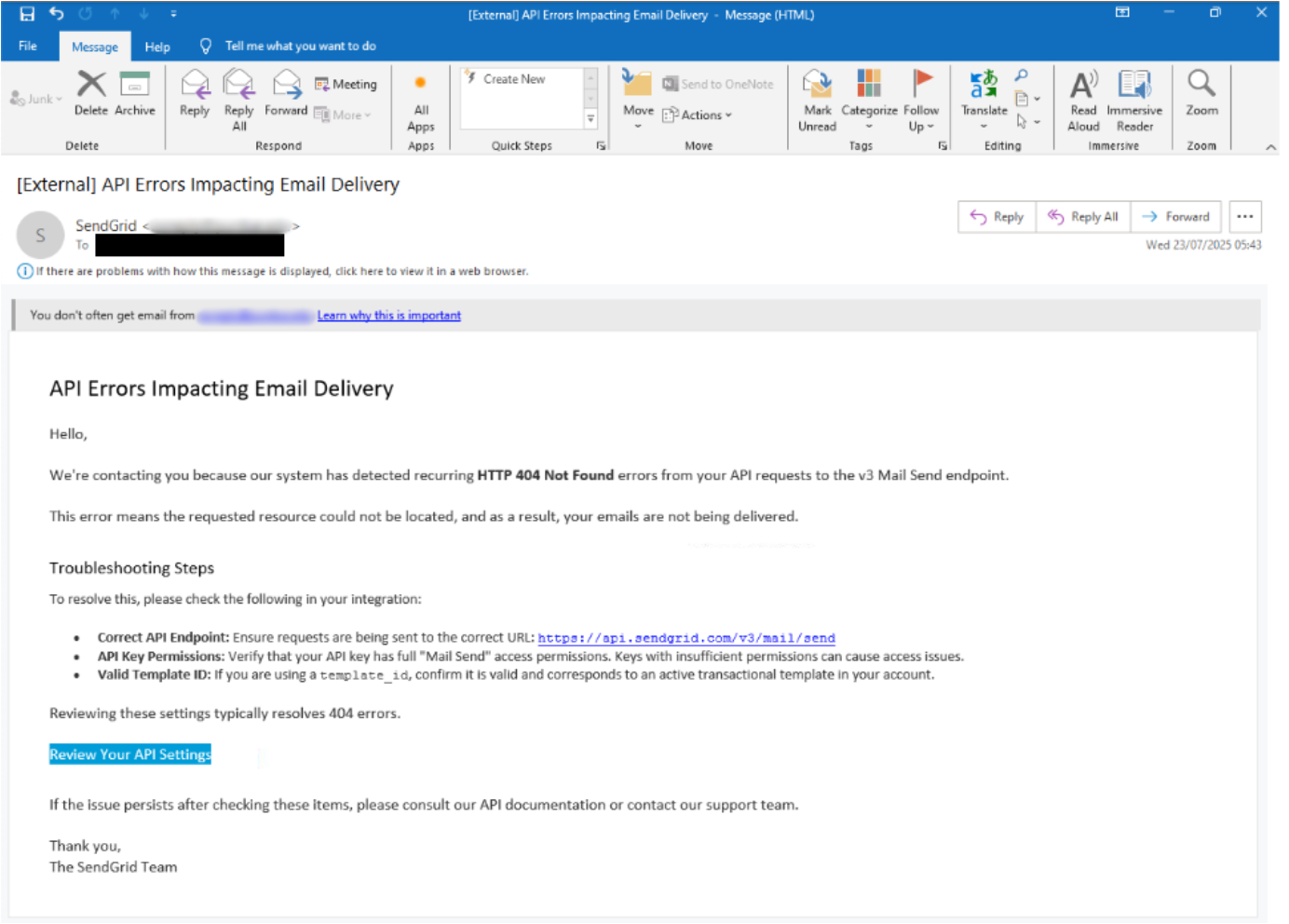
Figure 1: Phishing email with title 'API Errors Impacting Email Delivery'
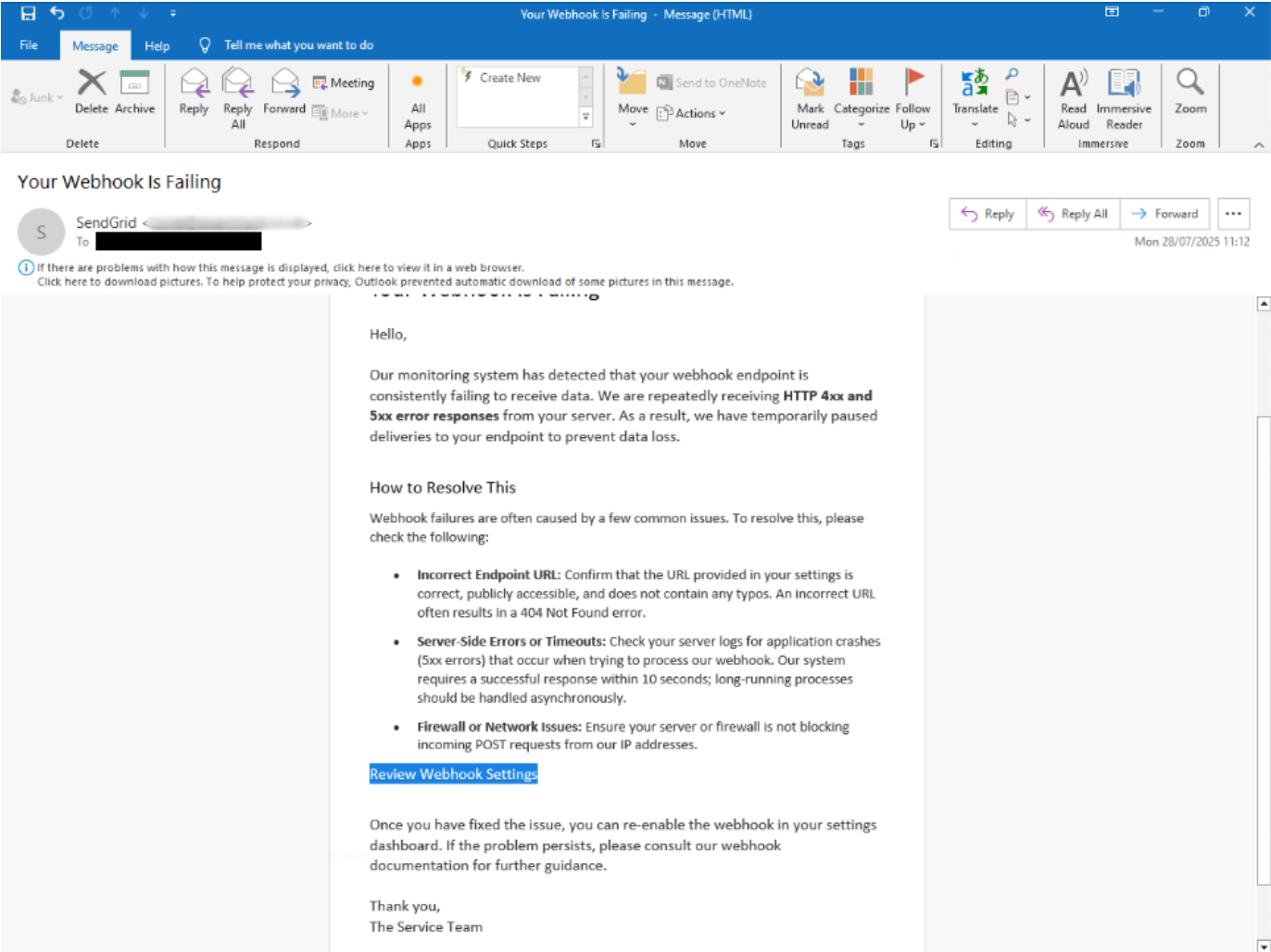
Figure 2: Phishing email with title 'Your Webhook Is Failing'
From there, BlueVoyant SOC analysts engaged the client to inform them of the potential credential harvesting issue and stop the attack while the TFC began uncovering the details of the broader campaign.
The malicious links leverage various legitimate email services capable of bypassing email filters to cloak the final spoofed login page destinations, including SendGrid’s service itself. Upon interacting with the phishing link, the user is directed to a CAPTCHA page to facilitate the deception, then served to a spoofed landing page that prompts the potential victim to enter their Twilio SendGrid credentials.
Spoofed Domains
- manage-sgdashboard[.]com
- dashboard-sgmanagement[.]com
- api-sendgridservice[.]com
- remote-sendgridlogin[.]com
- webhook-sendgridservice[.]com
- email-sendgridservice[.]com
- dashboard-sendgridlogin[.]com
- t-sendgrid[.]com
- https-sendgrid[.]com
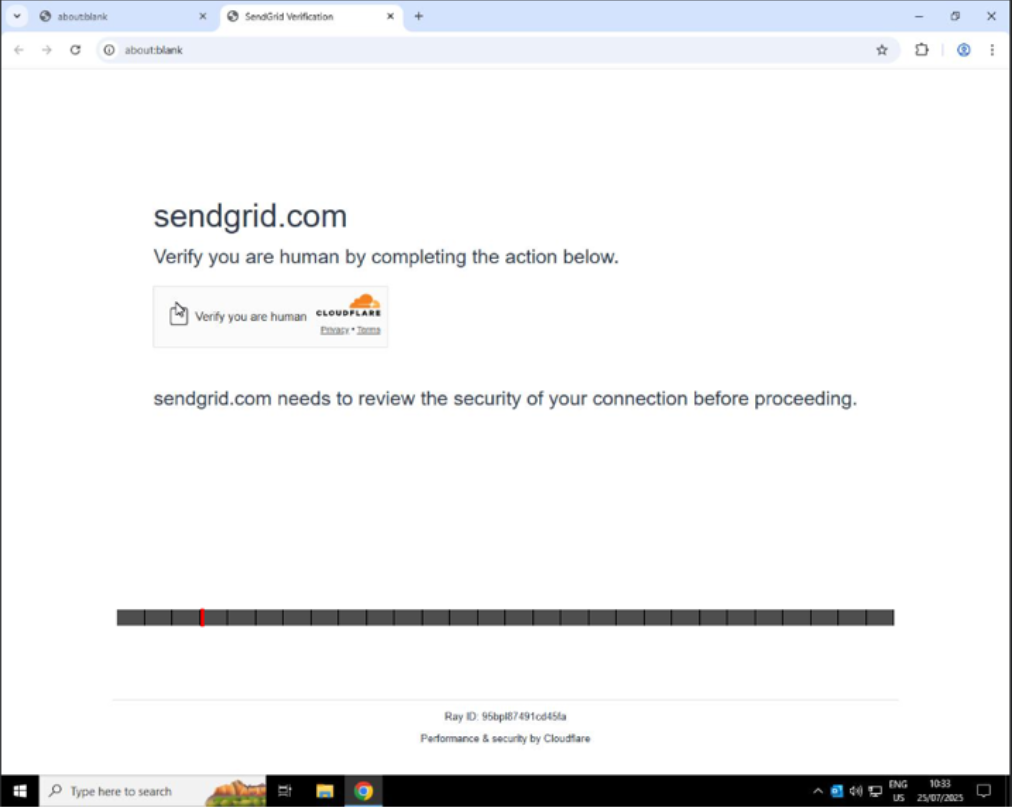
Figure 3: CAPTCHA Page
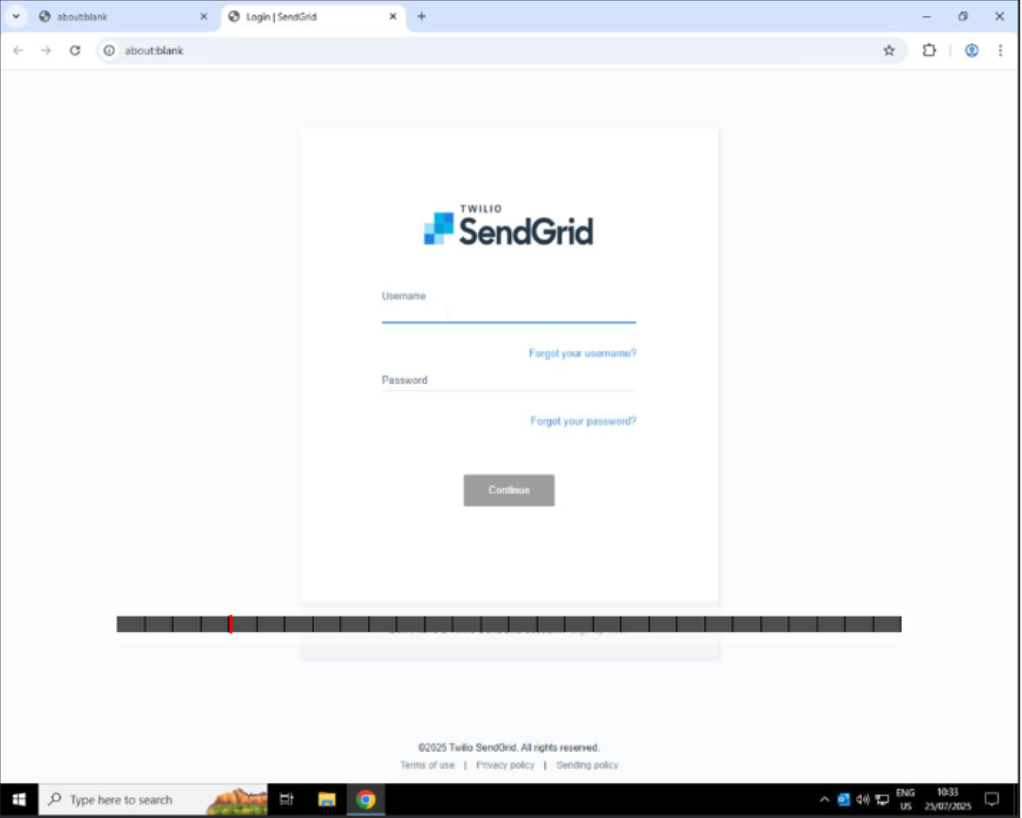
Figure 4: Twilio SendGrid Landing Page
Once the user enters their information, the attackers likely leverage SendGrid’s API to check if the credentials are valid as described by Netcraft in this somewhat similar campaign from February 2024. Kaspersky also reported in February 2024 on a credential harvesting lure that focused on establishing two-factor authentication (2FA) as the reason to click a link to a spoofed SendGrid landing page. Little other reporting has identified such attacks, and this may be the first reporting of attackers using these more technical sounding error messages to prompt user action.
The campaign appears to have begun around July 23 and activity appears to have stopped on 30 July. BlueVoyant has observed emails hitting users in more than 50 client environments spanning multiple sectors. It is unclear if the campaign is targeting specific users, although many of the targeted users the TFC identified were affiliated with IT departments. This makes sense as SendGrid users are often developers, IT admins, or platform managers — presumably, more security-savvy than the average user. This more technical lure may suggest threat actors understood this audience and tailored the social engineering approach as a result.
The TFC assigned the identifier UTG0198 to formally track this activity cluster. Given the campaign's novel tactics and dedicated infrastructure with no overlap to known actors, the TFC created this designation to consolidate future intelligence on this emerging threat and monitor its development.
How BlueVoyant is Keeping Clients Safe
BlueVoyant’s quick response to this attack attempt in a client’s environment stymied it before it launched; however, the attack serves to highlight how threat actors are increasingly targeting tools with high operational value (e.g., email services, cloud providers) rather than simply individual endpoints, maximizing “return on investment” per compromised account.
In this case, SendGrid accounts often hold API keys and SMTP credentials, which are harder to rotate than passwords and can grant persistent access even after password resets. This extends the attack lifecycle and complicates remediation. Furthermore, compromised SendGrid accounts could enable lateral attacks against customers of the breached company (e.g., password reset emails altered to redirect to phishing sites).
How to Prevent Email Phishing Attacks
To prevent such attacks, organizations should prioritize advanced email security measures, including DMARC/DKIM/SPF enforcement to combat domain spoofing and sandboxing of suspicious links to intercept cloaked phishing pages.
For SendGrid-specific protection, multi-factor authentication (MFA) and proactive API key rotation are critical, as static credentials or keys grant attackers persistent access even after password resets.
IT and developer teams should generally require specialized training to recognize technical social engineering lures, such as fabricated “webhook failures” or “API errors,” through simulated phishing drills. Adopting a zero-trust approach to link interaction — manually navigating to official portals instead of clicking embedded URLs — reduces risk, while least-privilege access controls and dark web monitoring limit exposure and detect credential leaks.
If you would like further guidance from BlueVoyant on simulated phishing drills/campaigns, adopting a zero trust approach, and/or dark web monitoring, then please contact us so we can help strengthen your security.
MITRE Techniques: T1078, T1204.001, T1583.001, T1566.002, T1566
Thomas Elkins is a Tier 3 SOC analyst, and Joshua Green is a principal security researcher.
Related Reading
Industry Insights
Ransomware in First Half of 2025: An Ecosystem in Flux
Managed Detection and Response
Why Microsoft Sentinel data lake Signals the Future of Security Operations