Industry Insights
Cybersecurity Maturity Model Certification - CMMC
April 5, 2020 | 4 min read
BlueVoyant

By Amy Williams, PhD, CISSP – Director of Proactive Services and Business Development
Federal contractors and subcontractors are direct targets of state sponsored cyber attacks. Moreover, evidence suggests that smaller organizations are larger targets because they tend to have immature security programs. Gaining access to data systems of a subcontractor that makes a unique component of proprietary military equipment, cyber thieves benefit two ways. First, they can steal the company’s intellectual property (IP), and second, they can leverage their access to escalate privileges beyond local systems and steal IP from other companies in the supply chain.
How Does this Happen?
The BlueVoyant Cyber Forensics and Incident Response team regularly sees phishing and social engineering used in combination with the deployment of sophisticated malware like Emotet to move quickly on to their next target once they have acquired a set of compromised credentials. A VPN with a weak password, email credentials found on the dark web, a poorly segmented guest network, or a convincing spear-phishing campaign can be enough to start a full-blown attack throughout the entire supply chain. Theft of American trade secrets is growing and now costs an estimated $300-600 Billion a year. That is why the Department of Defense (DoD) feels it’s critically important that we start making concerted efforts to help shore up the weakest links.What’s Being Done?
The DoD introduced the Cybersecurity Maturity Model Certification process (CMMC) as a means to certify that contractors are prepared to protect all Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) shared across the entire supply chain as well as put in place the required security controls to protect all intellectual property. CMMC expands on requirements outlined in Defense Federal Acquisition Regulation Supplement (DFARS), Code Of Federal Regulations (CFR), and National Institute of Standards and Technology (NIST) guidelines - specifically Special Publication (SP) 800-171Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations. CMMC attempts to consolidate cybersecurity requirements into a simplified model. CMMC consists of five different levels called “Maturity Levels”. Each level is additive, meaning you can’t be level 4 without being level 3, or level 5 without being level 4.What Does CMMC Mean To Contractors?
Contractors who do not meet certification requirements stand to lose contracts and the ability to work with the defense industry. Exactly how the DoD will assign maturity levels to specific contracts is currently being determined. If a company is unsure of which level they will be at, they should aim for the higher level. If a company wants to be more proactive in their cybersecurity, they should choose either level 4 or 5. If they expect that they will only need to meet compliance requirements, level 3 should be sufficient. Aiming for a higher level may open up future opportunities so there is no down side other than initial cost. It is very likely that small-to-midsize companies will have to increase their investment in security in order to meet the requirements if they are not already NIST 800-171 compliant. That said, it is also possible that some suppliers who do not handle sensitive information may actually get some relief in the expectations of cybersecurity requirements relative to their current situation. The goal of the maturity levels is to specify the requirements based on the sensitivity of information handled on a contract by contract basis. In addition, the CMMC level required for a prime contractor will not mean that all subcontractors must achieve that same level if the subcontractor isn’t handling sensitive information. We expect that most of our clients will strive to achieve ML3, which aligns closely with existing NIST 800-171. If you already have NIST 800-171 security controls in place, achieving CMMC ML3 will not be difficult to do.Now Is The Time To Work Towards Compliance.
Currently, DFARS and NIST SP 800-171 only require contractors to “self-certify” that they meet cybersecurity standards. CMMC will add a third-party verification (like BlueVoyant) process to that certification. If your cybersecurity policies are already aligned with the NIST framework, give yourself a pat on the back - you are well-positioned for CMMC compliance. The big difference will be the third-party verification/assessment required under CMMC. Although the CMMC rules are expected to be modified and improved as more is learned, once you are certified, that certification will be valid for 3 years.How BlueVoyant Can Help
The DoD acquisition team is encouraging companies to get started immediately on moving toward CMMC compliance by working with companies that have NIST 800-171 and cyber assessment experience. The BlueVoyant Professional Services team has extensive experience providing similar assessments including the NIST 800-171 assessment as well as our own proprietary Cybersecurity Maturity Assessment (CMA). Our team is currently providing proactive CMMC pre-assessments that include a detailed comparison of current states of cybersecurity posture and maturity against the CMMC framework controls associated with the maturity level that you wish to achieve. BlueVoyant is ready and waiting to help you get a jump on your competitors by ensuring that your security policies are in compliance with these new requirements. The final stages of assessor certification are expected to be completed by the DOD in April 2020. Clients who can show that they have the required controls in place will be able to fast track through the final assessment, saving time and ensuring that there are no gaps in their eligibility for contract opportunities.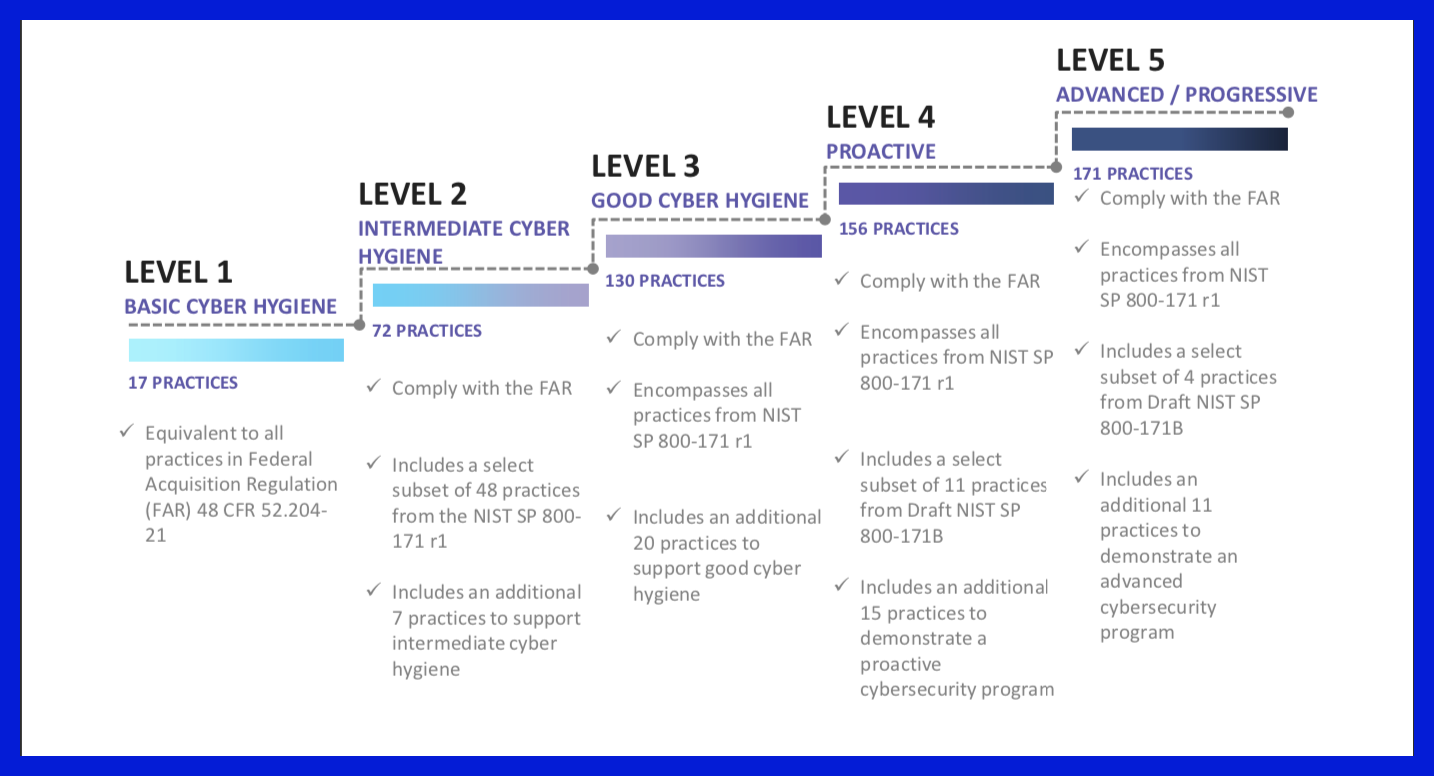
Related Reading
Industry Insights
Ransomware in First Half of 2025: An Ecosystem in Flux
Managed Detection and Response
Why Microsoft Sentinel data lake Signals the Future of Security Operations