Supply Chain Defense
Attack Vectors Using COVID-19
May 7, 2020 | 3 min read
BlueVoyant

“Life in the SOC” is a Blog Series that shares experiences of the BlueVoyant SOC defending against the current and prevalent attacks encountered by our clients. The blogs discuss successful detection, response and mitigation actions that can improve your defensive capabilities.
COVID-19 continues to dominate news headlines. It is having a major impact in the world of cybersecurity. Threat actors apply fear, uncertainty and doubt to enticing victims to perform certain actions. They have learned that the mere mention of COVID-19 is enough to solicit a quick click or prompt a user into action.
COVID-19 is being used in a variety of malicious campaigns including email spam, BEC (Business Email Compromise), malware, ransomware, and malicious domains. As the number of those afflicted continue to surge, so too do the campaigns using the disease as a lure. The following is a breakout of how COVID-19 is being used for different types of attack:
Spam/Phishing
Shelter-in-place is forcing users to increase their use of online tools. IT and Security teams need to be aware that cybercriminals are using popular online tools, sharing software, and file attachments in their phishing campaigns, including:
- Google Drive
- Trello
- Skype
- Zoom
- Salesforce
- Github
- Slack
- TeamViewer
We have seen an increase in spam messages that:
- Offer new information or updates on the virus after clicking on a link.
- Offer attachments to fill out forms for COVID-19 testing.
- Request donations in bitcoin to a wallet owned by the attackers.
There have been multiple spam campaigns related to shipping transactions, either postponements or shipping updates. One such campaign, under the guise of providing a new shipping schedule, contained malware.
Business Email Compromise
There are ongoing BEC scams making use of the disease. BEC schemes usually work by tricking targets into transferring money to a threat actor posing as someone from within the same company.
Malicious Websites
A large number of bogus COVID-19 related websites are registered everyday. Some are active and engaged in a variety of nefarious activities. One group of sites promoted an app that could be downloaded to “protect” users from COVID-19.
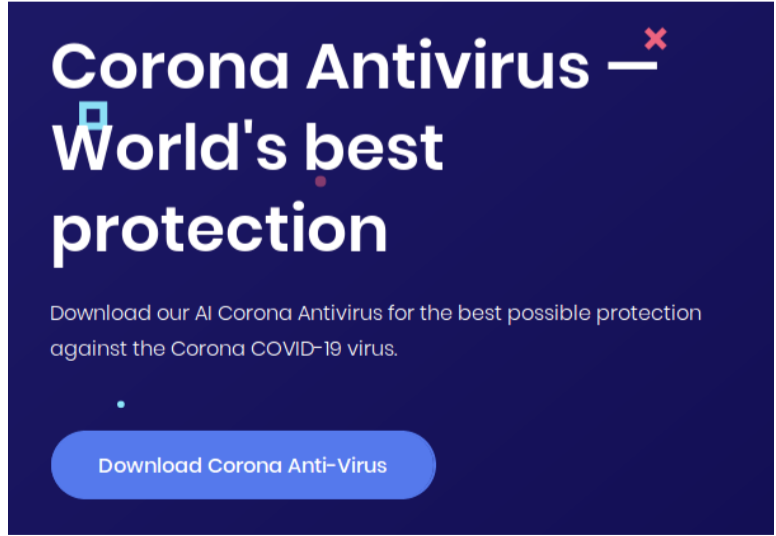
The websites claim the app is the result of the work from Harvard University. Installing the app infects the system with the BlackNET RAT malware, which adds the infected device to a botnet. In another campaign, a fake government website lures users with the promise of aid or relief by imitating legitimate "gov.uk" sites. It will ask for personal information and collect user bank account credentials after they enter a correct postcode.
The most popular theme has been malicious sites masquerading as video streaming sites offering free content. Malicious actors are aware that many users are quarantined and spending more time looking for online entertainment. Threat actors are using these sites to peddle malware, steal credentials, etc.
Malicious Social Media Messaging
In concert with the campaigns above, several other campaigns used social media messengers such as Facebook (FB) Messenger to lure victims to download malware, for example, with the promise of two months of free Netflix.

This particular campaign aims to get the user to log into their FB account in order to obtain the free trial subscription. It then captures the user’s credentials. We see these types of scams across all the major social media applications such as FB, Twitter, YouTube, and Instagram.
Malware
Brian Krebs, a high profile investigative reporter on cybercrime, reported on an interactive COVID-19 map produced by Johns Hopkins University. It was used in malicious websites (and possibly spam emails) to spread the AZORult malware. A member of several Russian language cybercrime forums began selling a digital Coronavirus infection kit that uses the interactive map as part of a Java-based malware deployment scheme. By late March, security experts began warning of new malicious websites using interactive versions of the same map to distract visitors while the sites tried to spread the password-stealing malware.
In another campaign, phishing emails delivered what was believed to be a COVID-19 tracker that turned out to be a coronavirus-themed Winlocker, an infection that effectively locks Windows. It prevents the user from accessing their desktop, files or applications. When executed, the malware drops files and modifies system registries. It then displays a message requiring a password to unlock the machine.
Mobile
CovidLock ransomware comes in the form of a malicious Android app that claims to help track cases of COVID-19. The ransomware locks the victim’s device and allows 48 hours to pay US $100 in bitcoin ransom to regain access. Threats include the deletion of data stored in the phone and the leak of social media account details. There are also reports of malicious Android apps offering safety masks. Unfortunately, the malicious app actually delivers an SMSTrojan that collects the victim's contact list and sends SMS messages to spread itself.
Related Reading

Microsoft
Microsoft Copilot for Security - Threat Intelligence Use Cases - Part 2
March 25, 2024 | 3 min read

Digital Risk Protection
BlueVoyant Identifies Novel Threat Actor Campaign Using Fake Law Firm Invoices to Launch Phishing Attacks
March 20, 2024 | 2 min read

